01_Unified Platform Architecture
A Layered Architecture for Cyber Resilience
The BluSapphire Unified Platform represents a paradigm shift in cybersecurity, moving from a complex, siloed security stack to a fully integrated, AI-driven system. This document details the platform's multi-layered architecture, designed to deliver comprehensive security from edge prevention to fully autonomous response.
Figure 1: The BluSapphire Unified Platform's integrated four-layer architecture.
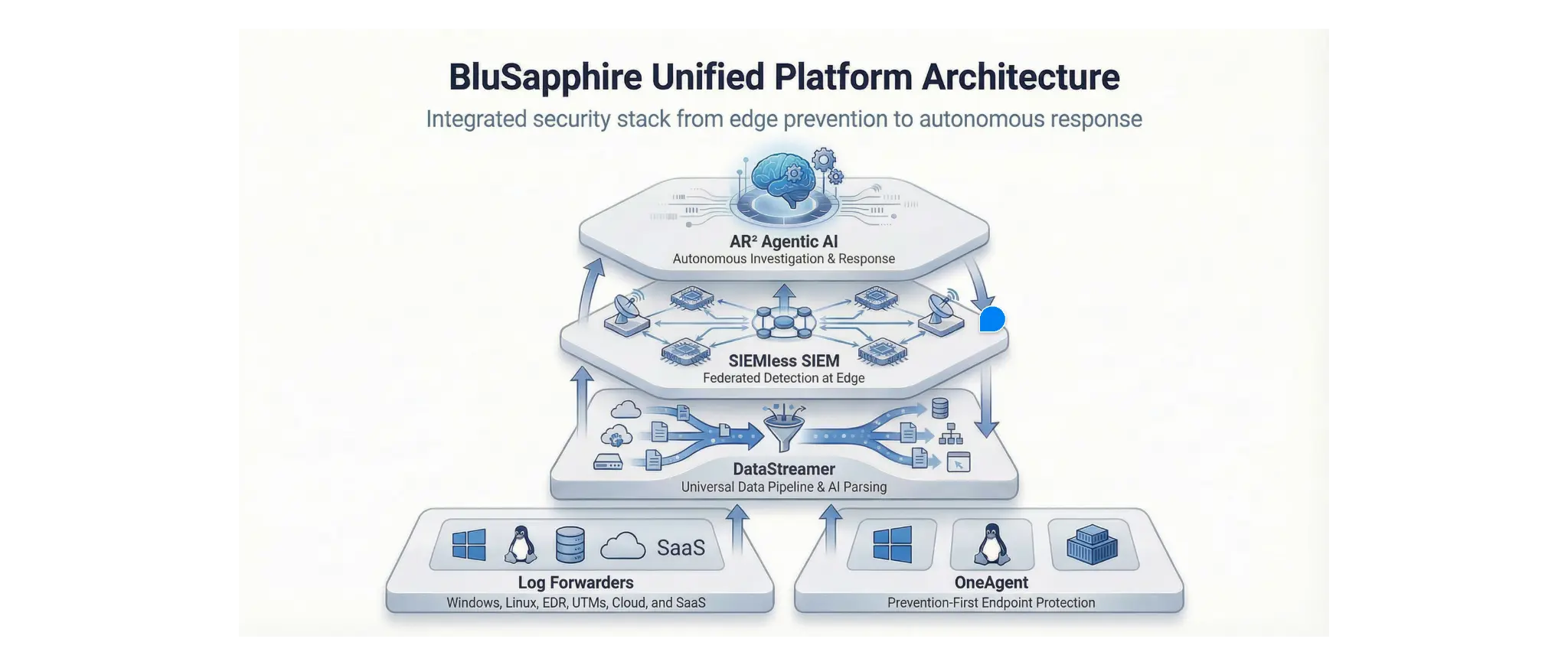
Architecture Overview
The platform is built on four distinct, yet deeply integrated, layers that work in concert to provide a seamless security workflow. Data flows from the foundational data source layer up to the autonomous response layer, with each step adding intelligence and context. This design eliminates the integration challenges and visibility gaps that plague traditional, multi-vendor security solutions.
Layer 1: Foundational Data Sources & Prevention
The architecture begins with a comprehensive data collection and prevention foundation, composed of two key components:
OneAgent: A prevention-first endpoint protection agent that provides robust defense against malware, exploits, and other endpoint-based threats. It acts as the first line of defense, stopping attacks before they can execute and feeding critical security telemetry into the platform.
Log Forwarders: The platform ingests data from a vast array of sources across the entire IT environment. This includes native support for Windows, Linux, EDR, UTMs, cloud infrastructure (AWS, Azure, GCP), and SaaS applications. This ensures complete visibility across all assets.
Layer 2: DataStreamer™ - Universal Data Pipeline & AI Parsing
Once collected, all data is funneled into the DataStreamer. This intelligent data pipeline is responsible for:
AI-Powered Parsing: Automatically parsing and structuring data from any source, without the need for complex, custom parsers.
Normalization: Transforming disparate data formats into a unified, query-able schema.
Efficient Routing: Intelligently routing data to the appropriate analysis and storage tiers, optimizing for both performance and cost.
This layer ensures that the data is clean, contextualized, and ready for high-speed analysis, eliminating the data wrangling that consumes significant resources in legacy SIEMs.
Layer 3: SIEMless SIEM™ - Federated Detection at the Edge
The structured data from the DataStreamer feeds into the SIEMless SIEM, the core detection engine of the platform. Its key capabilities include:
Federated Detection: A distributed architecture that allows for threat detection to occur at the edge, closer to the data source. This reduces latency and enables faster response times.
Advanced Analytics: Utilizes a combination of machine learning, behavioral analysis, and correlation rules to identify both known and unknown threats with high fidelity.
Real-time Correlation: Correlates events across multiple data sources in real-time to uncover complex attack patterns that would be missed by siloed tools.
Layer 4: AR² Agentic AI - Autonomous Investigation & Response
At the apex of the architecture is the AR² Agentic AI. This layer receives high-fidelity alerts and contextual data from the SIEMless SIEM and performs:
Autonomous Investigation: The AI agent automatically investigates alerts, gathering additional context, enriching data, and determining the full scope and impact of a threat.
Intelligent Response: Based on its investigation, the AI can execute a wide range of autonomous responses, from isolating an infected endpoint to blocking a malicious IP address at the firewall.
Human-in-the-Loop: While capable of full autonomy, the platform ensures that human analysts are always in control, with the ability to review, approve, or override any AI-driven action.
The Integrated Workflow: From Prevention to Response
The power of the Unified Platform lies in the seamless integration of these four layers:
Prevention & Collection
OneAgent blocks threats at the endpoint while Log Forwarders collect telemetry from across the enterprise.
Parsing & Normalization
DataStreamer ingests and prepares this data for analysis.
Detection & Correlation
The SIEMless SIEM analyzes the data to detect malicious activity.
Investigation & Response
The AR² Agentic AI autonomously investigates and neutralizes the threat.
This integrated workflow enables a response time of less than 2 minutes, a 98% reduction in Total Cost of Ownership (TCO) compared to traditional solutions and allows for up to 95% of security operations to be run autonomously.
Last updated